Networking is the backbone of any cloud infrastructure, and Microsoft Azure offers a comprehensive suite of networking services designed to meet even the most demanding enterprise requirements. In this article, we’ll explore the fundamental components of Azure networking and how to design robust, scalable network architectures.
Beyond the Basics: Azure Virtual Network Architecture
Azure Virtual Networks (VNets) are the cornerstone of networking in Azure. They provide isolation, segmentation, and serve as the boundary for resources deployed in Azure. However, truly effective enterprise architectures require a deeper understanding of VNet design principles.
Hub-and-Spoke Network Design
One of the most effective network topologies for enterprise environments is the hub-and-spoke model. This architecture consists of a central hub VNet connected to multiple spoke VNets, providing a scalable and manageable approach to network segmentation.
The hub-and-spoke model offers several advantages:
- Centralised control: Security services and shared resources can be placed in the hub, simplifying management.
- Cost optimisation: Shared services reduce duplication across environments.
- Simplified connectivity: New spokes can easily connect to on-premises networks through the hub.
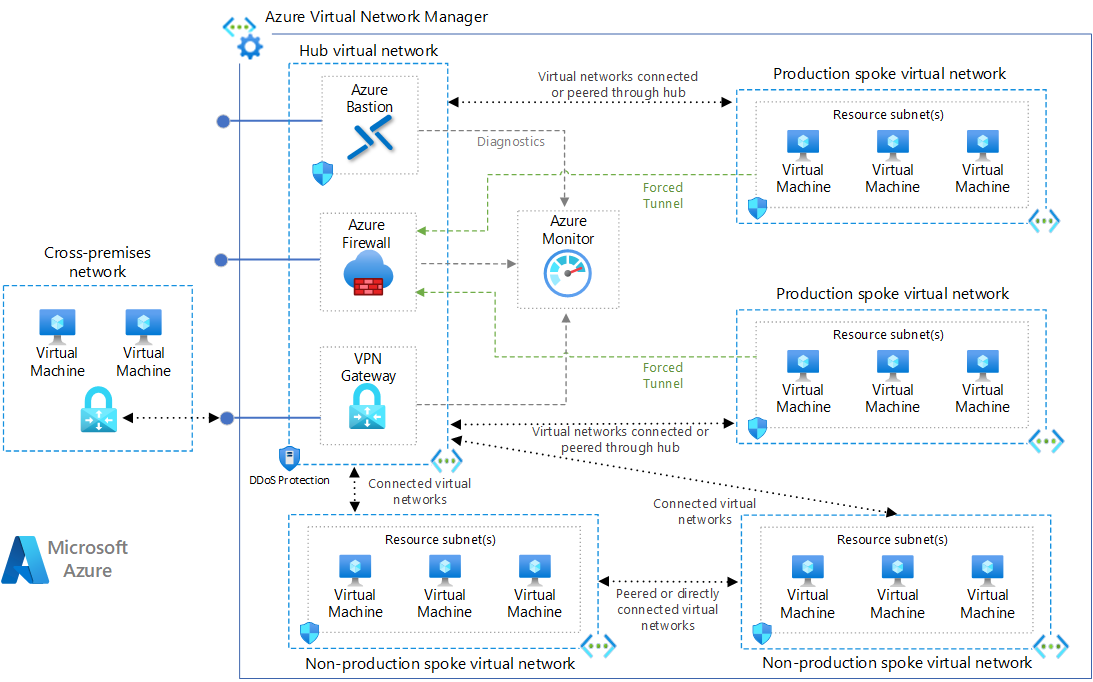
Source: Microsoft Azure Architecture Center
Implementing Hub-and-Spoke with Azure Virtual WAN
For organisations with complex networking requirements, Azure Virtual WAN provides an enhanced hub-and-spoke architecture managed as a service. It simplifies branch connectivity, optimises routing, and provides integrated security.
Here’s how a typical Virtual WAN hub might be configured:
## Create a new Virtual WAN
$virtualWan = New-AzVirtualWan -ResourceGroupName "enterprise-networking-rg" `
-Name "global-vwan" `
-Location "West Europe" `
-AllowBranchToBranchTraffic $True
## Create a Virtual WAN Hub
$virtualWanHub = New-AzVirtualHubVnetConnection -ResourceGroupName "enterprise-networking-rg" `
-VirtualWanName "global-vwan" `
-Name "europe-hub" `
-Location "West Europe" `
-AddressPrefix "10.0.0.0/23" `
-Sku "Standard"
## Connect a spoke VNet to the hub
$spokeVnet = Get-AzVirtualNetwork -Name "prod-vnet" -ResourceGroupName "prod-rg"
New-AzVirtualHubVnetConnection -ResourceGroupName "enterprise-networking-rg" `
-VirtualHubName "europe-hub" `
-Name "prod-connection" `
-RemoteVirtualNetwork $spokeVnetAdvanced Network Security in Azure
Network security in Azure goes well beyond traditional firewalls. A comprehensive approach involves multiple layers of protection.
Network Security Groups and Application Security Groups
Network Security Groups (NSGs) serve as virtual firewalls, filtering traffic to and from Azure resources. Application Security Groups (ASGs) extend this functionality by allowing you to group virtual machines and define network security policies based on those groups.
The following PowerShell script demonstrates how to create an NSG with rules that leverage ASGs:
## Create Application Security Groups
$webAsg = New-AzApplicationSecurityGroup -ResourceGroupName "app-rg" `
-Name "web-asg" `
-Location "North Europe"
$apiAsg = New-AzApplicationSecurityGroup -ResourceGroupName "app-rg" `
-Name "api-asg" `
-Location "North Europe"
## Create Network Security Group
$nsg = New-AzNetworkSecurityGroup -ResourceGroupName "app-rg" `
-Name "app-nsg" `
-Location "North Europe"
## Create NSG rule allowing HTTP traffic to web servers
$webRule = New-AzNetworkSecurityRuleConfig -Name "Allow-HTTP-Web" `
-Description "Allow HTTP to web layer" `
-Access Allow `
-Protocol Tcp `
-Direction Inbound `
-Priority 100 `
-SourceAddressPrefix Internet `
-SourcePortRange * `
-DestinationApplicationSecurityGroup $webAsg `
-DestinationPortRange 80
## Create NSG rule allowing traffic from web to API servers
$apiRule = New-AzNetworkSecurityRuleConfig -Name "Allow-Web-to-API" `
-Description "Allow web layer to API layer" `
-Access Allow `
-Protocol Tcp `
-Direction Inbound `
-Priority 110 `
-SourceApplicationSecurityGroup $webAsg `
-SourcePortRange * `
-DestinationApplicationSecurityGroup $apiAsg `
-DestinationPortRange 443
## Add rules to NSG
$nsg | Add-AzNetworkSecurityRuleConfig -NetworkSecurityRule $webRule
$nsg | Add-AzNetworkSecurityRuleConfig -NetworkSecurityRule $apiRule
$nsg | Set-AzNetworkSecurityGroupAzure Firewall and Azure Firewall Manager
For more advanced filtering capabilities, Azure Firewall provides a managed, cloud-based network security service that protects your Azure Virtual Network resources. Combined with Azure Firewall Manager, it enables centralised security policy management and traffic routing.
A notable feature is the ability to create hierarchical policies, where a base policy defines common rules, and application-specific policies inherit and extend those rules:
## Create base policy
$basePolicy = New-AzFirewallPolicy -Name "base-security-policy" `
-ResourceGroupName "security-rg" `
-Location "West Europe"
## Add a rule collection group to the base policy
$ruleCollectionGroup = New-AzFirewallPolicyRuleCollectionGroup -Name "core-rules" `
-Priority 100 `
-FirewallPolicyName "base-security-policy" `
-ResourceGroupName "security-rg"
## Create network rule collection
$networkRuleCollection = New-AzFirewallPolicyFilterRuleCollection -Name "network-rules" `
-Priority 100 `
-ActionType "Allow"
## Add a rule to allow outbound DNS
$networkRule = New-AzFirewallPolicyNetworkRule -Name "allow-dns" `
-Protocol "UDP" `
-SourceAddress "*" `
-DestinationAddress "8.8.8.8", "1.1.1.1" `
-DestinationPort "53"
$networkRuleCollection.Rules.Add($networkRule)
$ruleCollectionGroup.RuleCollection.Add($networkRuleCollection)
Set-AzFirewallPolicyRuleCollectionGroup -Name "core-rules" `
-FirewallPolicyName "base-security-policy" `
-ResourceGroupName "security-rg" `
-RuleCollection $ruleCollectionGroup.RuleCollection
## Create an application-specific policy that inherits from the base policy
$appPolicy = New-AzFirewallPolicy -Name "app-security-policy" `
-ResourceGroupName "app-rg" `
-Location "West Europe" `
-BasePolicy $basePolicy.IdPrivate Link and Private Endpoints
Azure Private Link provides secure access to Azure PaaS services over a private endpoint in your virtual network. This ensures that your traffic remains on the Microsoft backbone network, reducing exposure to the public internet.
The following PowerShell script demonstrates how to create a private endpoint for an Azure SQL database:
## Get the virtual network and subnet
$vnet = Get-AzVirtualNetwork -Name "app-vnet" -ResourceGroupName "app-rg"
$subnet = Get-AzVirtualNetworkSubnetConfig -Name "private-endpoint-subnet" -VirtualNetwork $vnet
## Get the SQL server resource ID
$sqlServer = Get-AzSqlServer -ResourceGroupName "data-rg" -ServerName "example-sql-server"
## Create private endpoint
$privateEndpointConnection = New-AzPrivateLinkServiceConnection -Name "sql-connection" `
-PrivateLinkServiceId $sqlServer.ResourceId `
-GroupId "sqlServer"
New-AzPrivateEndpoint -ResourceGroupName "app-rg" `
-Name "sql-endpoint" `
-Location "West Europe" `
-Subnet $subnet `
-PrivateLinkServiceConnection $privateEndpointConnectionAdvanced Networking Features for Enterprise Scale
Beyond the basics, Azure offers several advanced networking features crucial for enterprise deployments.
Global VNet Peering and Global Reach
Azure’s global infrastructure allows VNets in different regions to be connected via Global VNet Peering. For on-premises connections, ExpressRoute Global Reach enables connecting different ExpressRoute circuits, effectively connecting on-premises sites through the Microsoft backbone.
## Get virtual networks
$vnetEurope = Get-AzVirtualNetwork -Name "europe-vnet" -ResourceGroupName "europe-rg"
$vnetAsia = Get-AzVirtualNetwork -Name "asia-vnet" -ResourceGroupName "asia-rg"
## Create peering from Europe to Asia
Add-AzVirtualNetworkPeering -Name "europe-to-asia" `
-VirtualNetwork $vnetEurope `
-RemoteVirtualNetworkId $vnetAsia.Id `
-AllowForwardedTraffic `
-AllowGatewayTransit
## Create peering from Asia to Europe
Add-AzVirtualNetworkPeering -Name "asia-to-europe" `
-VirtualNetwork $vnetAsia `
-RemoteVirtualNetworkId $vnetEurope.Id `
-AllowForwardedTraffic `
-UseRemoteGatewaysLoad Balancing Options: Standard Load Balancer vs. Application Gateway
Azure offers multiple load balancing options, each suited to different scenarios:
- Azure Load Balancer (Layer 4): Ideal for distributing network traffic across VMs at the transport layer.
- Application Gateway (Layer 7): Provides application-level routing, web application firewall, and SSL termination.
For multi-region load balancing, Azure Front Door and Traffic Manager offer global solutions. The following script sets up an Application Gateway with multiple backend pools:
## Create an Application Gateway with WAF
$appGwConfig = New-AzApplicationGatewayWebApplicationFirewallConfiguration `
-Enabled $true `
-FirewallMode "Prevention" `
-RuleSetType "OWASP" `
-RuleSetVersion "3.1"
$sku = New-AzApplicationGatewaySku -Name "WAF_v2" -Tier "WAF_v2" -Capacity 2
$gw = New-AzApplicationGateway -Name "app-gateway" `
-ResourceGroupName "app-rg" `
-Location "West Europe" `
-BackendAddressPools $backendPool1, $backendPool2 `
-BackendHttpSettingsCollection $httpSettings `
-FrontendIPConfigurations $frontendIP `
-GatewayIPConfigurations $gatewayIP `
-FrontendPorts $frontendPort `
-HttpListeners $listener `
-RequestRoutingRules $rule `
-Sku $sku `
-WebApplicationFirewallConfig $appGwConfigAzure Route Server for BGP Routing
For complex routing scenarios, Azure Route Server enables using BGP to exchange routes between Network Virtual Appliances (NVAs) and your VNet. This allows for dynamic routing and integration with third-party networking solutions.
## Create Route Server
$routeServerSubnet = Get-AzVirtualNetworkSubnetConfig -Name "RouteServerSubnet" -VirtualNetwork $vnet
$routeServer = New-AzRouteServer -ResourceGroupName "networking-rg" `
-RouteServerName "hub-routeserver" `
-Location "West Europe" `
-HostedSubnet $routeServerSubnet.Id `
-PublicIpAddress $publicIP.Id
## Peer with NVA
Add-AzRouteServerPeer -ResourceGroupName "networking-rg" `
-RouteServerName "hub-routeserver" `
-PeerName "cisco-nva" `
-PeerIp "10.0.1.4" `
-PeerAsn 65001Network Monitoring and Troubleshooting
Robust monitoring is essential for maintaining a healthy network infrastructure. Azure offers several tools for this purpose:
- Network Watcher: Provides monitoring and diagnostic tools for network resources.
- Network Performance Monitor: Helps monitor network performance across hybrid environments.
- Traffic Analytics: Provides insights into network traffic patterns.
The following PowerShell script sets up Network Watcher packet capture for troubleshooting connectivity issues:
## Create a storage account for packet captures
$storageAccount = New-AzStorageAccount -ResourceGroupName "networking-rg" `
-Name "networkdiagnostics" `
-Location "West Europe" `
-SkuName "Standard_LRS" `
-Kind "StorageV2"
## Get the VM to monitor
$vm = Get-AzVM -Name "problem-vm" -ResourceGroupName "app-rg"
## Start packet capture
$filter1 = New-AzNetworkWatcherPacketCaptureFilterConfig -Protocol TCP -RemoteIPAddress "40.91.82.23" -LocalPort "443" -RemotePort "443"
$filter2 = New-AzNetworkWatcherPacketCaptureFilterConfig -Protocol UDP -LocalIPAddress "10.0.0.4" -RemoteIPAddress "10.0.0.8"
New-AzNetworkWatcherPacketCapture -NetworkWatcher $networkWatcher `
-TargetVirtualMachineId $vm.Id `
-PacketCaptureName "connection-problem-capture" `
-StorageAccountId $storageAccount.Id `
-TimeLimitInSeconds 60 `
-Filter $filter1, $filter2Network Design Best Practices
Based on our experience implementing enterprise networking solutions in Azure, here are some key best practices:
-
Plan your address space carefully: Allocate IP space with room for growth, avoiding overlaps with on-premises networks.
-
Implement a consistent naming convention: Standardise resource naming to improve manageability.
-
Use network security groups at both subnet and NIC levels: Implement defense in depth by applying security at multiple levels.
-
Leverage service tags and application security groups: Use these features to simplify security rule management.
-
Implement a hub-and-spoke topology for large deployments: This provides better isolation and control for enterprise environments.
-
Use Azure Private Link for PaaS services: Keep traffic on the Microsoft network instead of traversing the public internet.
-
Implement routing controls: Use User-Defined Routes (UDRs) and route tables to control traffic flow within your network.
-
Deploy resources across availability zones: For critical networking components like load balancers, ensure redundancy across zones.
-
Monitor network performance: Use Azure Network Watcher and Log Analytics to maintain visibility into your network.
-
Document your network architecture: Maintain up-to-date documentation of your network design, IP address allocation, and security rules.
Conclusion
Building robust, secure, and scalable network foundations in Azure requires a deep understanding of the available services and how they fit together. By implementing the hub-and-spoke architecture, leveraging advanced security features like Azure Firewall and Private Link, and following the best practices outlined in this article, you can create enterprise-grade network environments in Azure that meet the most demanding requirements.
As your Azure footprint grows, regular reviews of your networking design become increasingly important. Consider using Infrastructure as Code (IaC) tools like Azure Resource Manager templates or Terraform to maintain consistency and enable version control of your network infrastructure.
References
-
Microsoft. (2024). Azure Virtual Network Documentation. https://docs.microsoft.com/en-us/azure/virtual-network/
-
Microsoft. (2024). Azure Virtual WAN Documentation. https://docs.microsoft.com/en-us/azure/virtual-wan/
-
Microsoft. (2024). Hub-spoke network topology in Azure. https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/hybrid-networking/hub-spoke
-
Microsoft. (2024). Azure Firewall Documentation. https://docs.microsoft.com/en-us/azure/firewall/
-
Natarajan, S. (2022). Azure Networking Cookbook: Practical recipes for secure network infrastructure, connectivity, and high availability (2nd Edition). Packt Publishing.